How To Implement Zero Trust
Even If You Have Zero Budget

Is it just me or do you sometimes feel that cybersecurity companies dream up fancy new names for old security technologies, just so they can gobble up your entire security budget in one hit?
If you are you a CISO, planning to spend your security budget by the end of the year, what will your favourite account manager try to sell you this Christmas?
And if you have already blown the budget, but not on Zero Trust, then hopefully this article will help.
First off, what is Zero Trust?
It’s a security concept that says that access is not granted even if a user is connected to a particular network.
A user must be still verified using strong authentication and compliance with security policies checked, before granting access. And then the least privileged access necessary is granted.
Security policies might include mandatory disk encryption, a certain version of OS, or an active firewall.
So who is giving away Zero Trust for free?
None other than Cloudflare.
In case you've never heard of Cloudflare, they are known as the world's best provider of website acceleration and protection services.
I’m talking about CDNs (Content Delivery Networks), DDoS (Distributed Denial of Service) protection, web application firewalls (WAFs), and so on.
But did you know that they also provide many other services?
Interestingly they now provide a Zero Trust Service for up to 50 users, completely free of charge.
I seem to remember that Duo Security had a similar offer with multi-factor authentication (MFA) before they were acquired by Cisco.
In the Cloudflare Zero Trust SaaS service, everything is managed from an easy-to-use dashboard.
So what exactly can you do with this free service?
First, Cloudflare’s Zero Trust can replace or augment your VPN.
Why would you want to replace or augment your VPN?
Well, many organisations realised during the recent pandemic that with so many people needing to work at home, additional VPN capacity had to be put in place quickly.
What’s the problem with that?
Anything done in haste is often done badly.
The issue is that many organisations now have generic VPN access policies that are so broad, that for example, their accounts department employees may be able to reach the development team's resources, whilst working from home.
That means lateral movement is easier during a cyber-attack.
Once an attacker compromises one user’s workstation at home, they can then move quickly throughout the organisation.
But there’s more to Cloudflare's Zero Trust than just this.
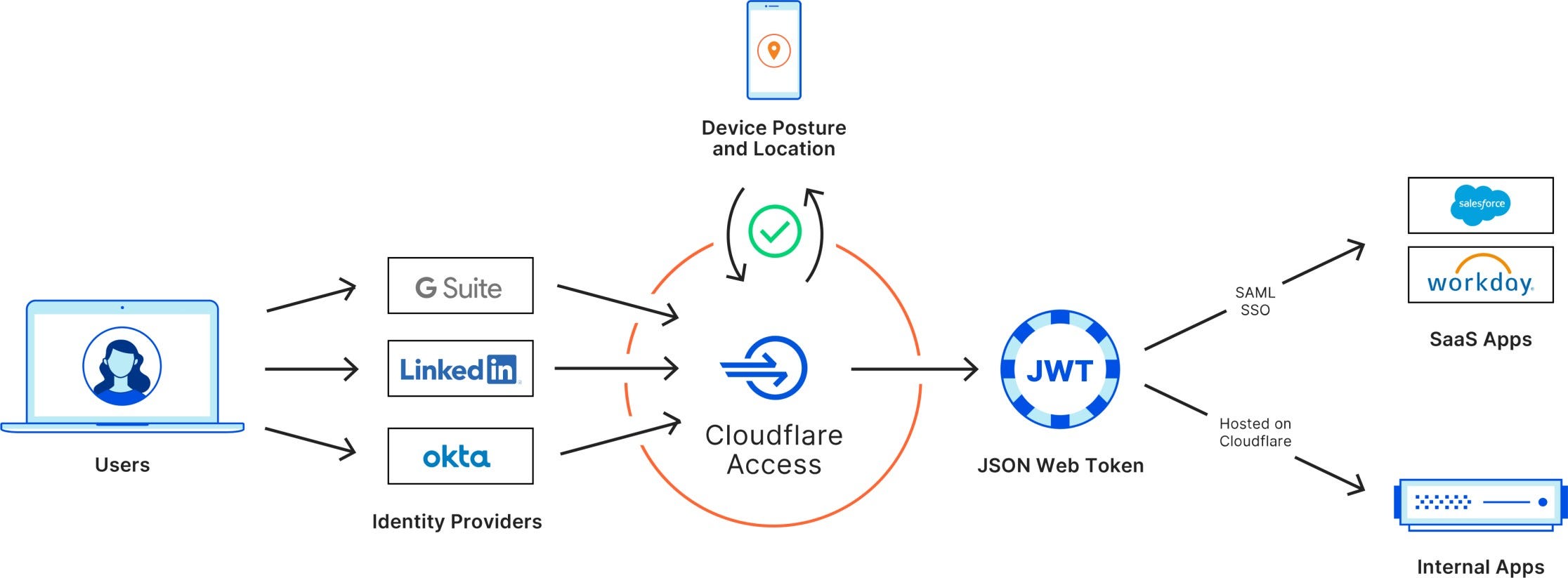
You enrol users in your organisation using Cloudflare’s Warp clients for MAC, PC and mobile platforms.
Once you have configured your policies, all users' web requests are sent via Cloudflare’s DNS filtering service.
The result is a bit like what Websense did back in the day. You select the website categories you want to block, and that’s it.
You can do the same for malware.
Effectively internet browsing can be intercepted, to block phishing and malware attacks before they can deliver their payload.
But that's not all.
You can protect your SaaS and on-premises apps too.
Cloudflare Zero Trust integrates with popular identity providers and then interacts with the web app using secure JSON web tokens.
So, what’s the catch?
Like any freemium SaaS offering, there is only documentation and community support for the 50 free user plan. Logging is also limited to 24 hours.
Not an issue, I managed to set it up and test it in the afternoon (and write this article).
The pay-as-you-go plan costs $7 per user per month, and gets you support, better features and more logging.
One of the best-paid features is called remote browser isolation, and it costs an additional $10 per month per user.
The idea behind browser isolation is to create a kind of virtual air gap between a user’s web browser and the endpoint device thereby protecting the user's endpoint and the enterprise network from threats.
You can also add more features like CASB (Cloud Access Security Broker) and DLP (Data Loss Prevention) in the custom contract plan.
I have been using Cloudflare with SaaS services for 6 or 7 years, and in my experience, Cloudflare's strengths are (i) security, (ii) ease of use and (iii) speed.
Setting up their services is trivial too when compared to working with comparable AWS offerings for example, and once you are using their services your users will get a reliable and responsive experience.
In my opinion, this Cloudflare offering is simply the best way to get Zero Trust.
"But free Zero Trust for 50 users is a no-brainer if you have Zero budget"
You can easily set up a proof of concept in an afternoon. But it's even better if you are an entrepreneur or small business. In that case, you can probably skip the PoC and go straight to Prod.
In any case, it's a great Zero Trust service, so if you are a customer with more than 50 users you will probably want to keep it anyway.





