Issue #2: Fortinet Vulnerabilities & Did Weaponised Toothbrushes Really Attack a Swiss Company?
Last Week's Vulnerabilities, Exploits, Ransomware, Data Theft, Industry News and a big fine for Amazon in France

The Latest Critical Vulnerabilities
Fortinet SSL VPN & SIEM
In a plot fit for a Hollywood science fiction movie, last week we heard about a recent alleged DDoS attack against a Swiss company, caused by no less than an army of hijacked toothbrushes.
The story about a Distributed Denial of Service (DDoS) attack using three million electric toothbrushes on a Swiss company, initially reported in this article by the Swiss newspaper Aargauer Zeitung and attributed to an employee of the Cyber Security firm Fortinet, has been widely disputed and is untrue
The narrative seems to have stemmed from a misunderstanding of a hypothetical scenario shared by a Fortinet employee, which was then incorrectly reported as an actual event.
Perhaps Fortinet would do better focusing on helping their customers eliminate vulnerabilities in their products, instead of blabbing to newspapers about imaginary DDoS attacks by toothbrushes.
Speaking of vulnerabilities, here are 4 nice critical vulnerabilities that emerged last week.
FortiOS &SSL VPN
| CVE | Type | CVSS Score |
|---|---|---|
| CVE-2024-21762 | Out-of-bounds Write | Critical |
| CVE-2024-23113 | Arbitrary code execution | Critical |
FortiSIEM
| CVE | Type | CVSS Score |
|---|---|---|
| CVE-2024-23108 | OS Command Injection | Critical |
| CVE-2024-23109 | OS command injection | Critical |
Yet Another Ivanti Vulnerability
Just when you thought you had fixed all of the recent vulnerabilities in your Ivanti solutions, along comes another Critical.
| CVE | Type | CVSS Score |
|---|---|---|
| CVE-2024-22024 | Authentication Bypass | Critical |
Fewer versions are vulnerable, and admins that applied the updated mitigation provided on 31st January are automatically protected.
But no need to relax just yet. According to Shadow server honeypot attack statistics at the time of writing, attackers were actively probing for this vulnerability on February 10th, and in the EU especially in Germany.
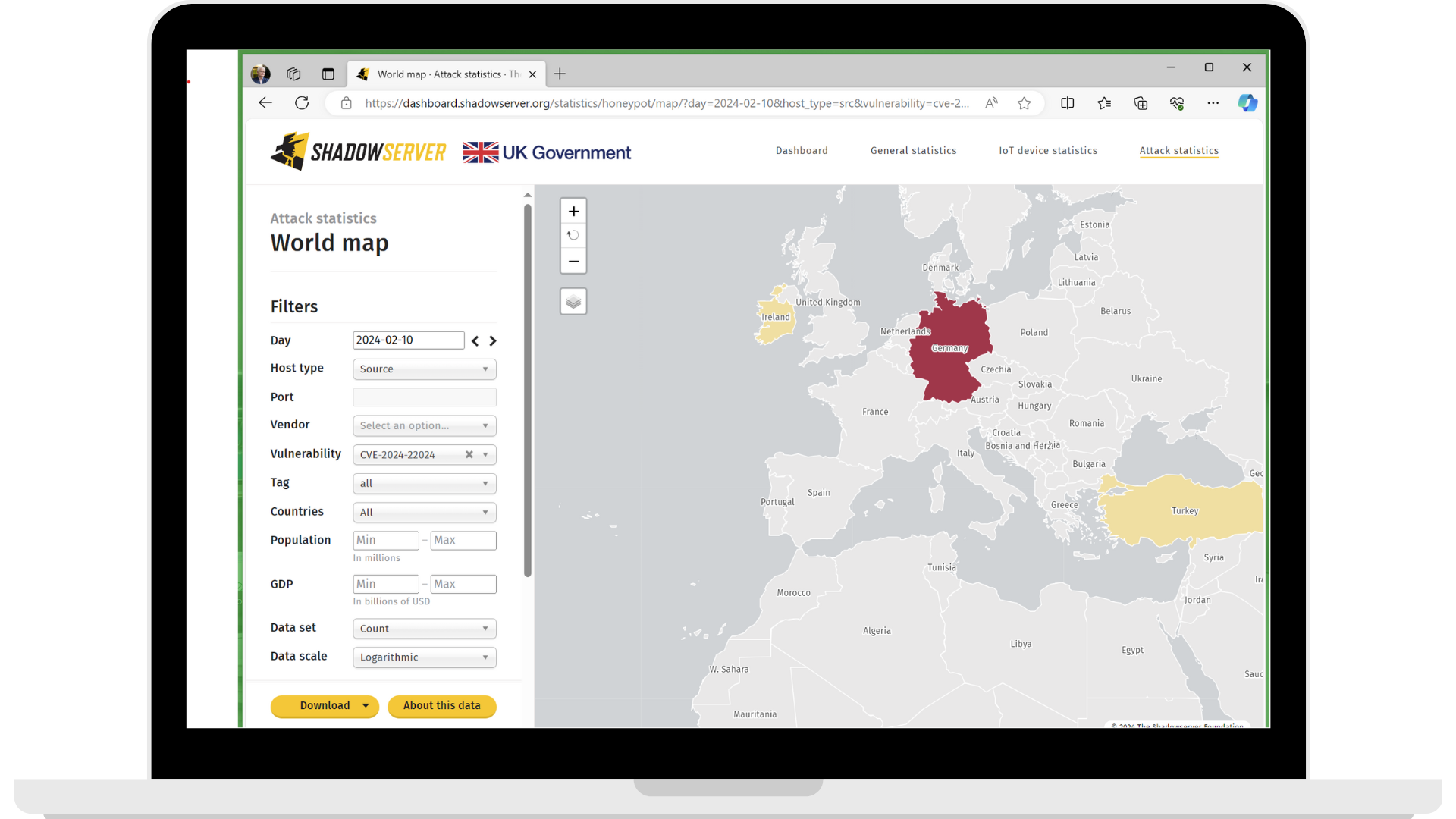
Whoever next. Cisco maybe?
Old Cisco ASA Vulnerabilities Targeted
The LockBit ransomware group is said to be exploiting older vulnerabilities in Cisco ASA SSL VPN devices, targeting flaws patched in 2020 and 2023.
| CVE | Type | CVSS Score |
|---|---|---|
| CVE-2020-3259 | Enumeration | High |
| CVE-2020-3580 | Enumeration / Cross-Site Scripting (XSS) | Medium |
Despite there being available fixes, many organizations, are still leaving themselves open to threats from these unpatched vulnerabilities and brute-force attacks.
Security teams would be well advised to patch or upgrade Cisco ASA devices, especially those with internet-exposed AnyConnect SSL VPN features.
Internet Facing TeamCity Servers Vulnerable
If you are a developer or DevOps Engineer, then this next one might interest you.
JetBrains has patched a critical security vulnerability in its TeamCity on-prem server that can allow unauthenticated remote attackers to gain control over a vulnerable server and use it to perform further malicious activity within an organization's environment.
TeamCity is a software development lifecycle (SDLC) management platform that thousands of organizations use to automate processes to build, test, and deploy software. It hosts sensitive data like source code and signing certificates.
Here are the details.
| CVE | Type | CVSS Score |
|---|---|---|
| CVE-2024-23917 | Authentication Bypass | Critical |
JetBrains identified the flaw in January. It affects all versions from 2017.1 through 2023.11.2 of its TeamCity On-Premises continuous integration and delivery (CI/CD) server.
The vulnerability could enable an unauthenticated attacker with web access to a TeamCity server to bypass authentication and gain administrative control of the server.
JetBrains already has released an update that addresses the issue.
Recent Ransomware Attacks
Hyundai Meets Black Basta
Hyundai Motor Europe was recently targeted by the Black Basta ransomware group, resulting in a significant cybersecurity breach. The attackers claim to have stolen around three terabytes of data from the company.
While initially described as just IT outages, the company later admitted the cyberattack and is currently investigating the unauthorized access to its network.
This incident, identified at the start of January, marks a concerning event for Hyundai, which had previously suffered a data breach in 2023 affecting customers in Italy and France.
The Black Basta group, known for its aggressive ransomware tactics and potential links to the infamous Conti ransomware group, employs double-extortion methods, threatening to leak stolen data unless a ransom is paid.
Ransomware Hits the Dead in Austria
In a humorous yet startling turn of events, a ransomware attack in an Austrian municipality has brought to light that not even the deceased can escape the clutches of Cyber criminals.
The incident resulted in the temporary cancellation of funerals, proving that even in today's age of AI, the dead might just have to wait a bit longer to find peace.
It seems that Cyber Security, or the lack of it, can indeed follow you to the grave.
Banking News
Cyber War Games at UAE Banks
In a pioneering initiative in the Middle East, the Central Bank of the UAE, conducted a Cyber War gaming exercise to evaluate and enhance the UAE banking sector's resilience against sophisticated cyber threats.
Key participants included major UAE bank representatives, financial and technology institutions, strategic partners, and cybersecurity experts.
This exercise emphasised the importance of information sharing, and collaboration for enhancing cyber resilience, and tested banks' incident response and crisis management skills.
Hong Kong Bank Tricked into $25 Million Hoist with AI Deep Fake
A Hong Kong firm recently reported a $25 million loss from a fraud involving deepfake technology, which was used to generate a fake video of the CFO and transmit this via a video conference.
This marks a significant evolution in Cybercrime using AI, the incident highlights the increasing threat of AI-powered fraud, and the need for financial entities to bolster their defences against such sophisticated attacks.
The technology, while not yet capable of real-time deepfake creation for ad-hoc conversations, is advancing quickly, urging companies to improve verification processes and adopt AI-driven security measures to combat emerging threats.
Recent Data Theft Incidents
2 Million Jobseekers Targeted in Asia
Last week it emerged that in the last two months of 2023, a cybercrime group targeted job seekers across Asia by hacking into job boards and recruiters' websites to steal personal information.
Using SQL injection and Cross-Site Scripting (XSS) attacks, they obtained over two million email addresses, along with names, phone numbers, dates of birth, and employment histories.
The attacks began as early as January 2023 and were primarily focused on the APAC region. The gang's activities were traced to a Chinese-language Telegram account selling the stolen data.
French Personal Data Stolen from Healthcare Insurers
In a significant cybersecurity incident, the personal data of 33 million French citizens was put at risk after breaches at two health insurance operators, Viamedis and Almerys, late last month.
The breaches potentially exposed names, birthdates, and social security numbers, though financial and medical information remained secure.
France's data privacy watchdog, CNIL, has initiated an investigation for GDPR violations and emphasizes the responsibility of health insurers to notify affected customers.
Amidst the turmoil, there's been misinformation about checking affected status, with CNIL advising vigilance and regular account monitoring for those potentially impacted.
Verizon Insider Caught with 60,000 Employees' Data
Verizon disclosed an internal data breach affecting more than 60,000 employees, where personal information such as names, addresses, Social Security numbers, and salary details were exposed due to unauthorised access by an insider.
It seems that an employee broke company policy and exported mass personal data of the company's employees onto a file, and handled that data inappropriately.
Discovered on December 12, 2023, but occurring around September 21, 2023, Verizon has taken steps to enhance security measures and is offering free identity protection to the impacted individuals.
The company believes there was no malicious intent behind the breach and no evidence suggests the information has been misused or shared externally.
This incident highlights the importance of ensuring that organisations implement Data Loss Prevention (DLP) systems as well as classifying data appropriately.
A Data Loss Prevention (DLP) system is designed to detect and prevent unauthorised access or sharing of sensitive information. It helps organizations protect their data by monitoring, detecting, and blocking transfer of sensitive data).
DLP solutions enforce data security policies to prevent accidental or malicious data breaches or leaks.
Data Protection
Danish Schools Ordered to Stop Sharing Data with Google
Danish authorities have directed schools to cease transmitting student data to Google, citing concerns over the company's handling of personal information which conflicts with European data protection standards.
This decision, influenced by the Danish Data Protection Agency's assessment, emphasizes the necessity for educational institutions to prioritize the security and privacy of student data.
Unfortunately, as Google Chromebooks are widely used in Danish schools, it will be extremely difficult to guarantee that schools have complied with the directive without banning the use of Chromebooks in schools altogether.
A Hefty Fine for Amazon in France
Amazon faces a €32 million fine from France's CNIL for excessive employee monitoring in its warehouses. The fine addresses issues like the over-collection of data through hand scanners and video surveillance, lack of data minimisation, and inadequate transparency and security measures.
Criticisms of Amazon's workplace practices, including the high pace demanded of workers, played a role in the investigation. Amazon plans to appeal the fine but has agreed to modify some monitoring practices.
This fine adds to Amazon's history of GDPR penalties, emphasising ongoing concerns about privacy and data protection practices within the company.





