BookPhish Targets Hotels & Guests
in Payment Card Fraud

Just as you thought you had heard of every conceivable type of Cyber Attack, say hello to BookPhish.
What the hell is BookPhish?
It’s a new twist on the Island Hopping Supply Chain Attack.
But of course, there are many different definitions for a Supply Chain Attack, and many are based on software coding and distribution. But there are other types.
In a classic Island island-hopping attack, hackers target big companies by first breaching smaller, less secure businesses in their network. Think of it as a game of digital leapfrog, where attackers jump from one organisation to another, getting closer to their main target.
These attacks often go after major organizations that work with a lot of suppliers or partners, like service providers, tech vendors, and business allies. These smaller entities are usually linked remotely to centralised applications and databases, creating lots of vulnerabilities for hackers to exploit.
Who is being Targeted?
If you ever stayed in a hotel, you have probably used Booking.com to reserve your room. Hotels use their services to manage bookings, collect payments and communicate with guests.
Recently guests have been receiving direct messages from hotels they just booked, inside the Booking mobile app, threatening to cancel rooms, unless the guest clicks on links to confirm payment.
This is classic Phishing but via this new indirect variant on the classic Supply Chain Attack.
So, let’s call it BookPhish.
Déjà vu?
Primarily it targets hotel managers, and if their email addresses weren’t stolen in an earlier Booking.com data breach, they probably find them on LinkedIn or Google.
Booking.com is no newbie to data breaches by the way.
As far back as 2013, Prestige Software, the company responsible for the Booking.com hotel reservation system, was storing customer data for its Cloud Hospitality system on badly configured Amazon S3 storage, exposing highly sensitive credit card data from millions of hotel guests worldwide.
An ethical hacker working for a US intelligence agency breached the servers of Booking.com in 2016 and stole user data related to the Middle East. The company decided to keep the incident secret.
Booking.com also suffered another data breach back in 2018 when telephone scammers targeted 40 employees at various hotels in the United Arab Emirates (UAE). After hackers obtained login credentials for the Booking.com system, they were able to access the personal details of over 4,100 customers who had booked a hotel room in the UAE via the site.
The company was hit with a €475,000 fine after failing to report this data breach within the time mandated in the EU GDPR Regulations.
So, why does BookPhish Attack work?
It uses social engineering to take advantage of busy hotel managers that can run the biggest five-star hotels, in the blink of an eye but may not be exactly IT literate.
I mean how many front-end developers do you know that can make their bed in the morning or cook a decent breakfast?
The hotel manager unknowingly gives the attacker the login to the Booking.com management application via a phishing link in an email, and from there the attacker starts sending guests phishing messages, asking for credit card details.
Here’s an example.
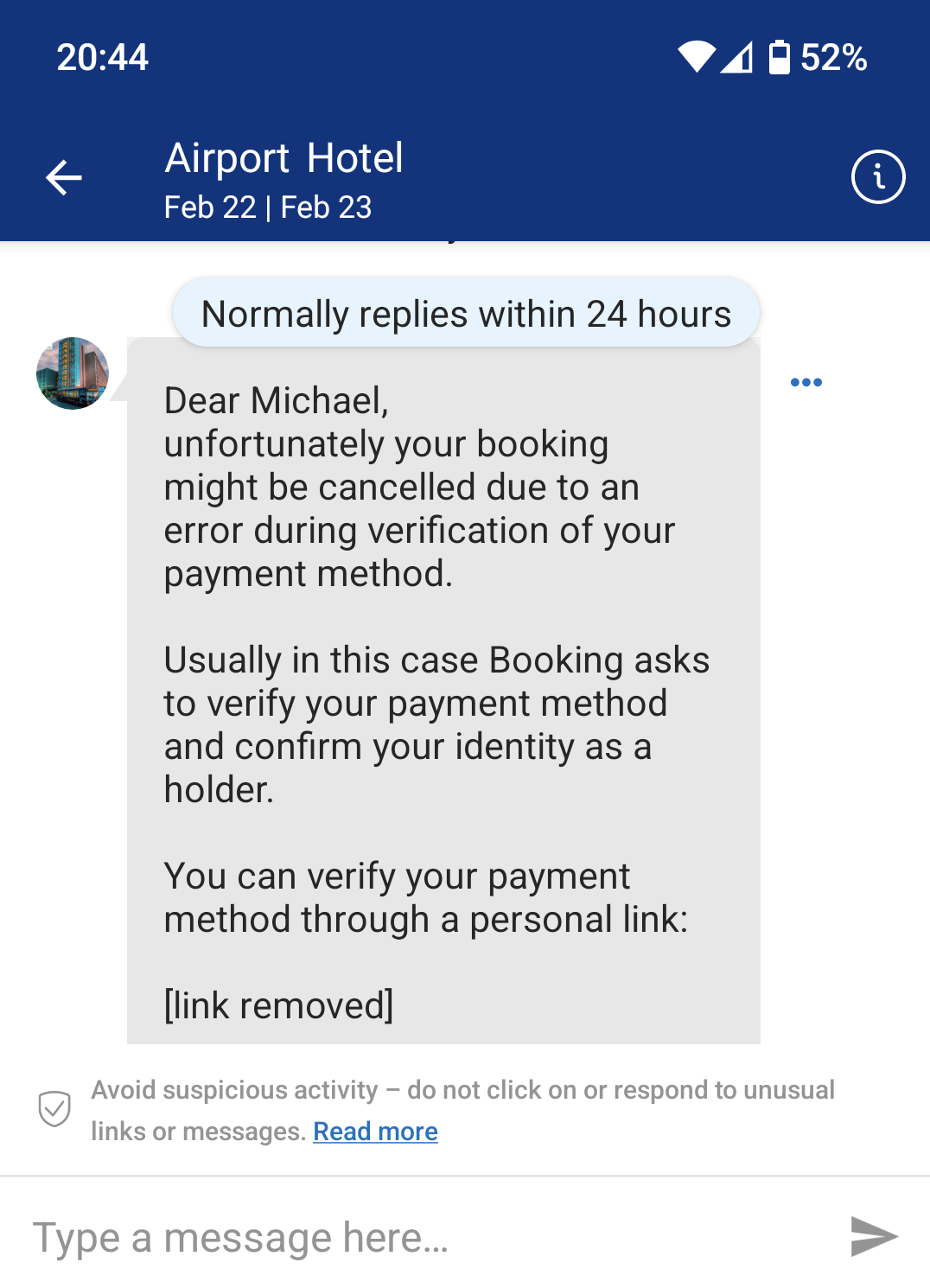
What is being done to remediate this attack?
From the messages I have seen, the malicious link in the email and direct messages from Booking.com are being replaced with [link removed]
So, it looks like it is being dealt with in the application.
And hotels are reacting quickly by sending out warning messages.
They are also being extremely wary of phone calls, and will not discuss bookings without calling you back.
So it looks like at least some hotels are on the case.
So how can you avoid getting BookPhished?
Let’s not forget that Phishing and Social Engineering are the bread and butter for hackers.
And they can write JavaScript in their sleep.
But often, they can’t spell.
So, looking at the English grammar and spelling in a message or email is often a good telltale sign.
If in doubt you should always call the hotel before handing over your card details outside the Booking.com app.
And given their history of past data breaches, perhaps it’s time to delete your stored cards from their website.
So, is BookPhish still a thing?
If the phishing links are now removed from all direct messages and emails to guests, then probably not, but the root cause has not gone away.
Hotel employees are still the weakest link, and Booking.com can probably do more to protect their applications from BookPhishing.
Perhaps hardware two-factor authentication like YubiKey can help resolve this.
In the meantime, if you are a hotel manager, what can you do?
Improved Cyber Security Awareness that targets hotel employees specifically is going to make a big difference.
If you found this article useful, please share it.
Thank you for reading Cyber Essentials. This post is public so feel free to share it.





